CSSCurrent en:Antivirus Software
General
Antivirus software ClamAV is installed on all Cryptshare appliances as a standard. All ClamAV versions as well as the database of the virus signatures are updated automatically.
Check status
ClamAV Daemon clamd
To check the current status of the ClamAV service, execute command 'systemctl status clamd.service'.
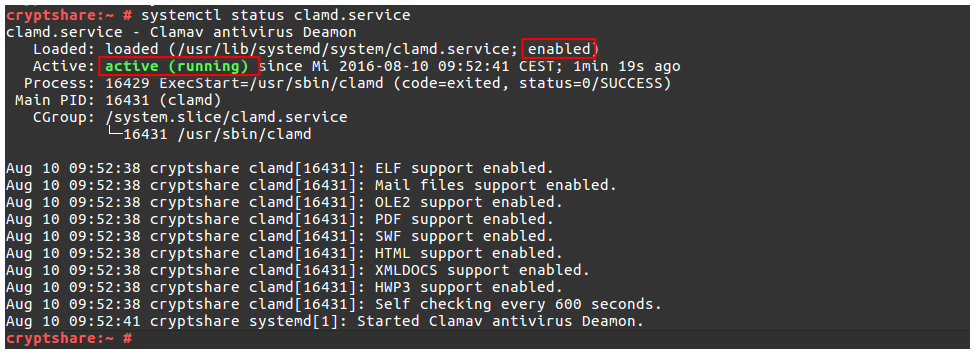 The service needs to be enabled and active as a standard. If this is not the case, you can activate the service with the command 'systemctl enable clamd.service' for its automated startup and start the service with the command 'systemctl start clamd.service'.
The service needs to be enabled and active as a standard. If this is not the case, you can activate the service with the command 'systemctl enable clamd.service' for its automated startup and start the service with the command 'systemctl start clamd.service'.
Update Daemon freshclam
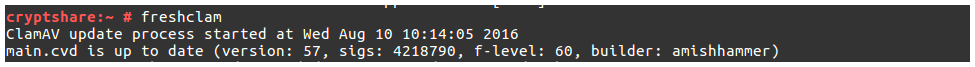
Update Daemon freshclam ensures that the virus signature database of ClamAV stays up to date and is executed every two hours. You can also start the Daemon manually with the command 'frehsclam'.
Logging
The results of the execution of 'freshclam' and a self-test of 'clamd' are logged in the file '/var/log/mail':
Creating your own signatures
If you want to block files of a certain type in transfers, you can create your own signatures.
General
A signature for ClamAV is a text file that has different contents and file endings, depending on the type of signature.
File type
ClamAV differentiates between the following file types:
- 0 every file
- 1 executable files (Portable Executable, 32-bit and 64-bit)
- 2 files in the OLE2 container that is used with Microsoft (MS Office, msi files, VBS)
- 3 HTML files
- 4 mail files
- 5 pictures and graphs
- 6 ELF (Executable and Linkable Format, .o, .so, .elf, .prx)
- 7 ASCII text files
- 8 not used
- 9 Mach-O files
The file type is recognised due to the information in the file header. With Linux, the hexadecimal value of a header can be displayed via ‘hexdump <file> | head -1’. Example: The header for the files .exe, .dll, .sys and .drv is 00000 4D5A 9000 0300 0000 0400 0000 FFFF 0000
Create signature
To create a signature for recognising certain files, the format ‚Extended signature format‘ can be used: MalwareName:TargetType:Offset:HexSignature
- MalwareName – the information displayed when recognizing the file, for instance in the console when opening ‚clamscan <file>‘
- TargetType – file type
- Offset – indicates how ‚HexSignature‘ is processed, for instance \* stands for each occurrence
- HexSignature is the hexadecimal value of an expression that is searched for in all scanned files, for instance 4d5a90000300 from the header of Portable Executable files.
Example
Signatures are stored under openSUSE in the directory ‘/var/lib/clamav’. If you want to categorise Portable Executable files as dangerous:
- Create a signature file ‘forbid\_portable\_executable.ndb’ in /var/lib/clamav
- Copy the following content into this file
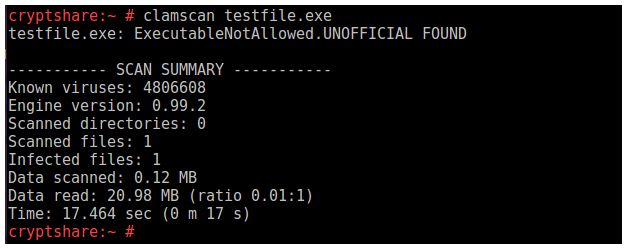
‘ExecutableNotAllowed:1:\*:4d5a90000300’
- Restart the service clamd ‘/etc/init.d/clamd restart’
- When opening clamscan, the following notification appears: